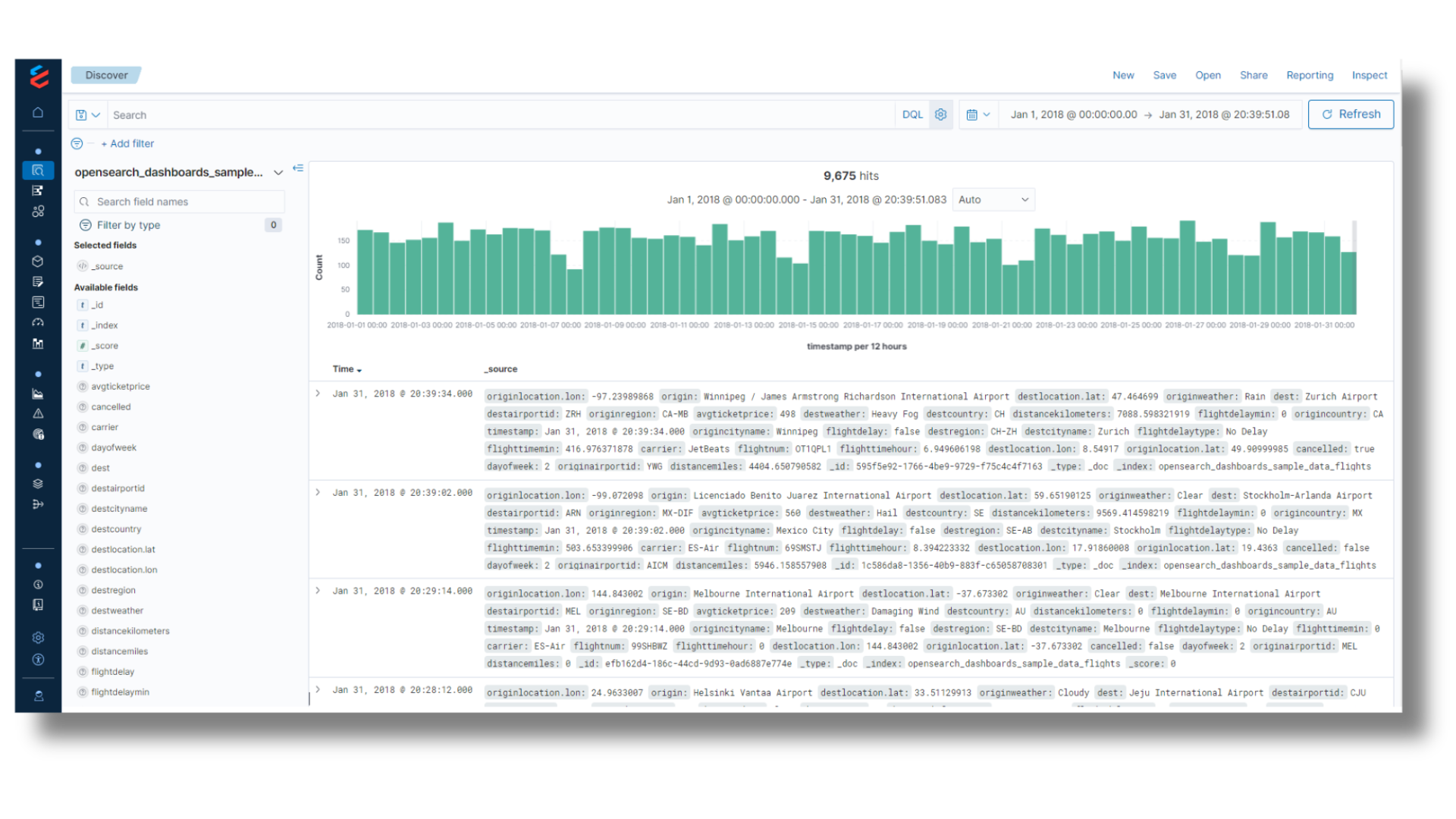
Log Management
Enable security analytics directly within the data lake. Eliminate the need to move data to separate analytics platforms.
Power of Open Search.
On unlimited history.
Elysium Search
Full visibility on ALL your data in your enterprise
- Integrated with Cloud Data Platform for a unified source of truth across IT, Security, and DevOps.
- Full text search with a single open standard query language (KQL) across cloud, third-party SaaS, and on-prem environments
- Effortlessly generate custom rules in seconds – without mastering a proprietary query language
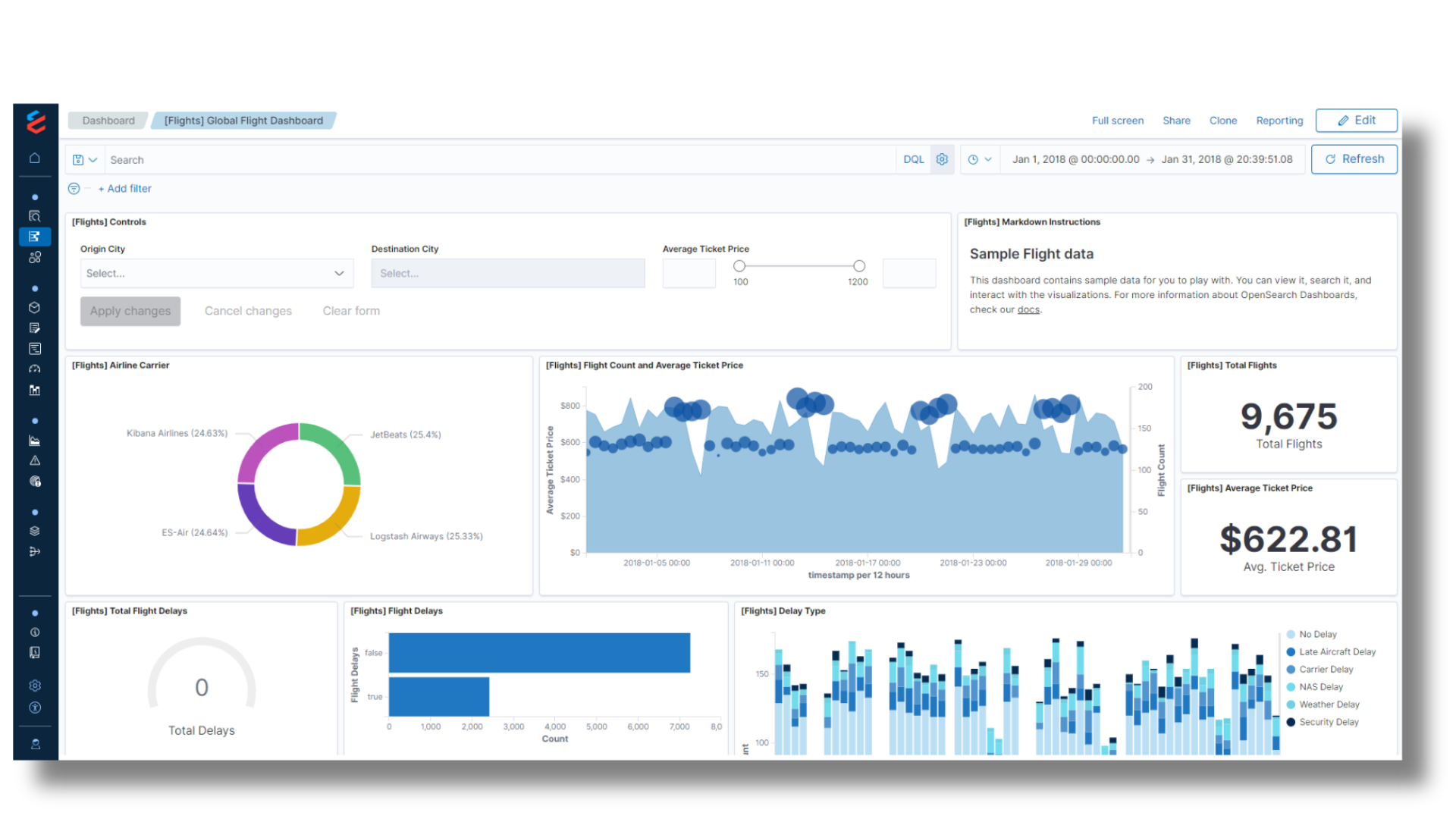
Dashboards and Visualization
Empower analysts with self-service dashboards
- Utilize preconfigured Looker and OpenSearch dashboards or create custom ones tailored to your needs.
- Enjoy the familiar flexibility of OpenSearch Dashboards for efficient data search and exploration.
- Drive monitoring, compliance, and exploration through Looker and OpenSearch Dashboards’ versatile analytics interface.
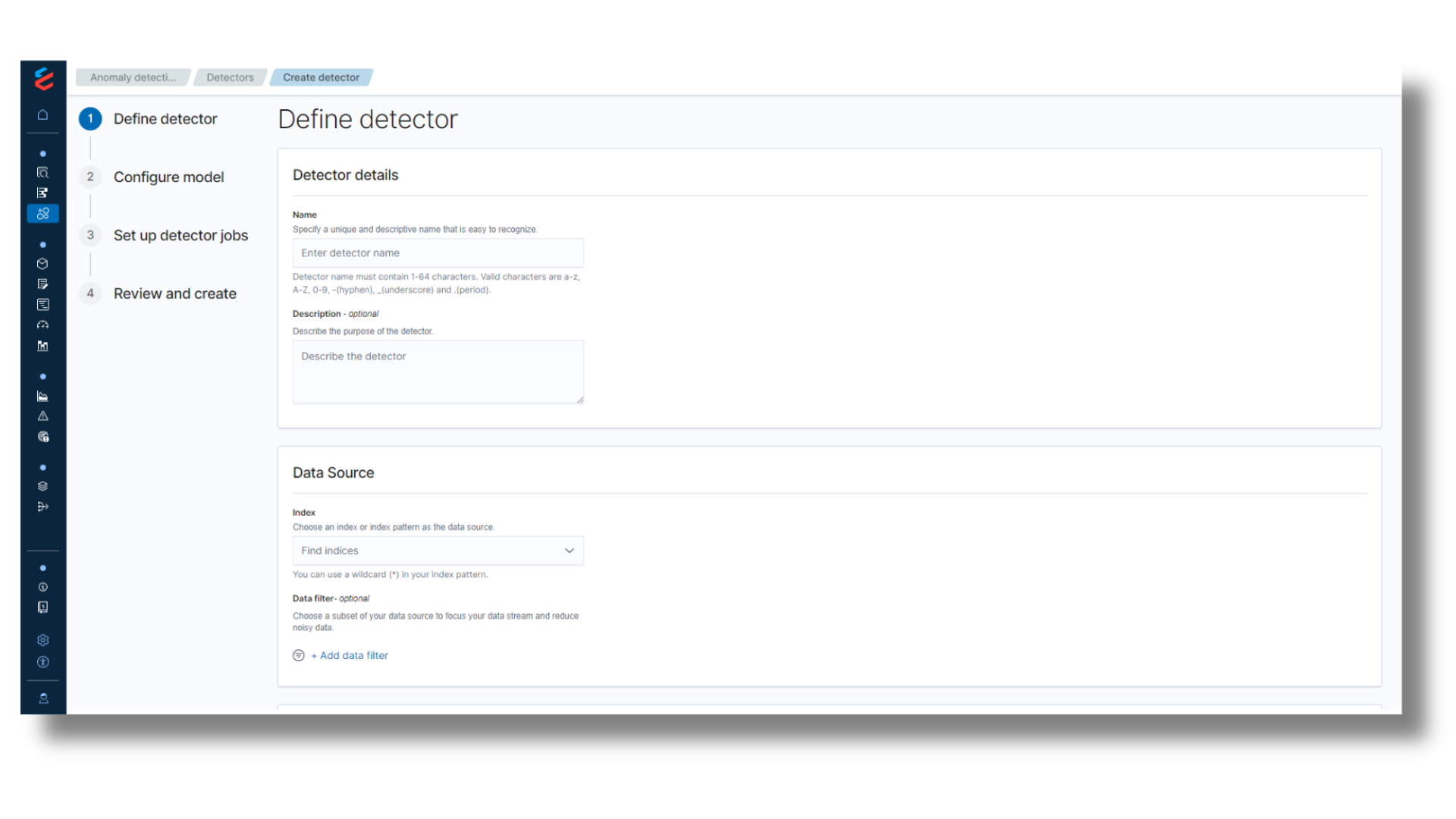
Anomaly Detection
Uncover hidden activities with zero code
- Detect potential threats across the full stream of ingested data
- Analyze everything and retain all the data on Snowflake’s low-cost data cloud
- Receive actionable alerts on malicious or anomalous patterns as data is received in near real time