Splunk
Store Petabytes of hot data in your Data Lake for the price of archival storage and eliminate cache churn and rehydration.
Search on Petabytes. From within Splunk.
Connect Security Data Lake to Your Splunk Implementation
Although substantially lower-cost storage and faster query response will have significant positive impact on security operations, any change to the SOC infrastructure must have minimal impact on the SOC workflow to be successful. With vertically integrated solutions where the application vendor has full control of storage, applications, APIs, and the user interface, it is often challenging to customize the solution to fit your needs.
Benefits of
Elysium Analytics
Splunk Add On
Unlimited
query compute
Query from Splunk on Snowflake data with elastic compute for consistent performance, scaling up and out as needed to ensure reliability under any workload.
Unlimited hot
storage
Elysium Analytics leverages Snowflake’s optimized object storage for a cost-efficient security data lake, ensuring seamless searchability and scalability for Splunk.
Open data model
Unify security telemetry with our open data model for effective threat detection, rich context, and simplified analytics sharing.
Data integrity
and compliance
Unmatched security features baked in from the start. Achieve compliance, protect your data, and focus on analysis.
Zero operational
overhead
Accelerate insights with Elysium’s effortless data ingestion, transformation, and delivery. Free up data engineers to focus on high-value activities.
Go Beyond Splunk
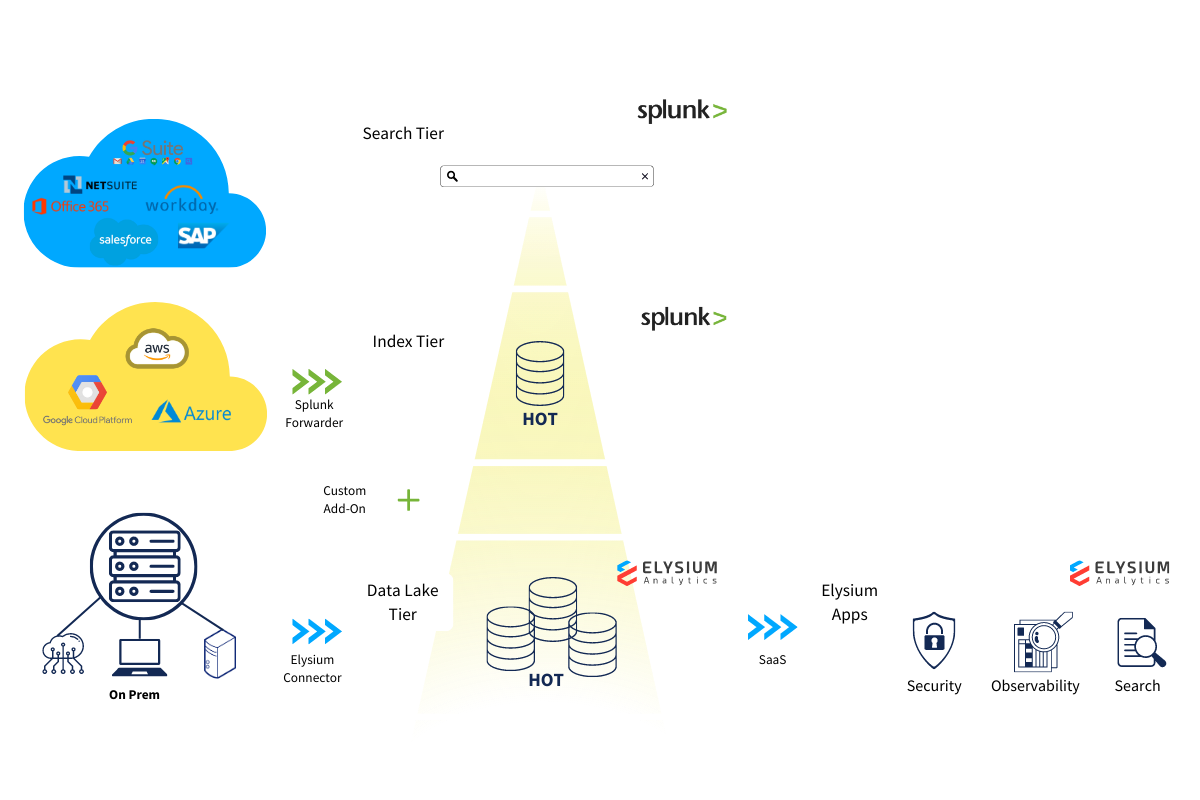
Load data from Splunk; Load data directly from log sources
Load data from Splunk with Universal Forwarder or Data Stream Processor to Elysium Analytics for long term retention of hot data in Snowflake. Then add all the data sources you are not ingesting to Splunk for a single source of truth security data lake searchable from Splunk.
Apply advanced analytics, dashboards, graph, alerting across all your data
With your log data in Snowflake, you now have the freedom to apply advanced ML-based analytics for anomaly detection and alerting across all your telemetry. Build your own dashboards with OpenSearch Dashboards or Looker, set behavioral and rule-based alerting, and conduct threat investigations, threat hunting, and monitoring with months, or even years, of data instantly available. Want options: Full-text search and SQL are also available.