Security Analytics
Enable security analytics directly within the data lake. Eliminate the need to move data to separate analytics platforms.
Unlimited Data Retention. Unparalleled Visibility.
Unified Open Data Model
Out-of-the-box Semantic Layer
- Elysium’s open data model integrates security telemetry for more effective threat detection, reducing dwell times.
- Elysium enables sharing and and reusing of model, algorithm, and analytics for threat detection.
- Enterprises can view the flow of all entities connected to this user and understand the severity of the “finding” as well as entities affected by it.
- Enhance your understanding of security threats by establishing context across telemetry and enrichment data
ML powered UEBA
Baseline User and Entity Behaviours Across the Enterprise
- Detect potential threats across the full stream of ingested data
- Analyze everything and retain all the data on Snowflake’s low-cost data cloud
- Machine Learning detectors utilize UEBA and anomaly detection to find suspicious signals
- Receive actionable alerts on malicious or anomalous patterns as data is received in near real time
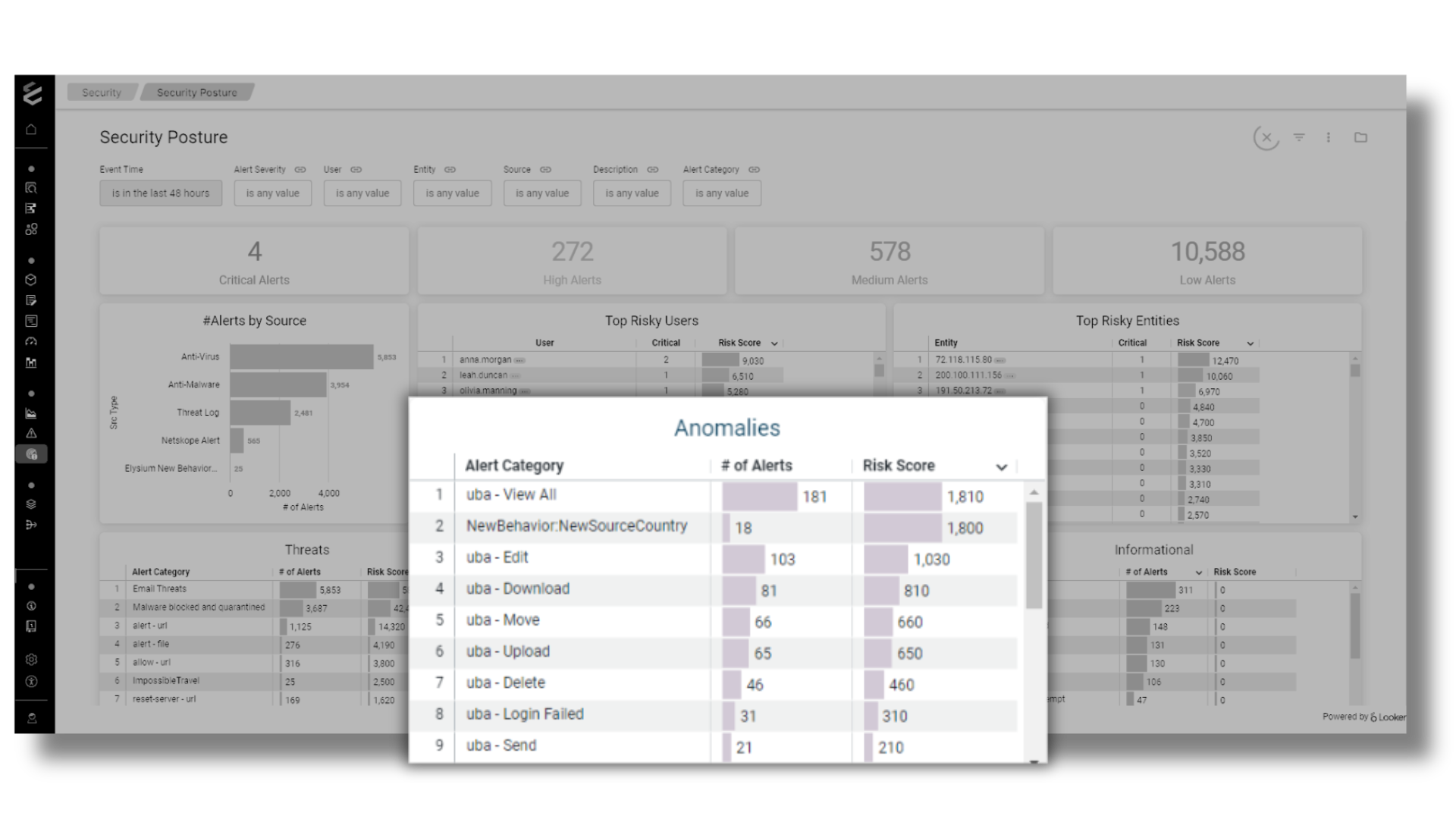
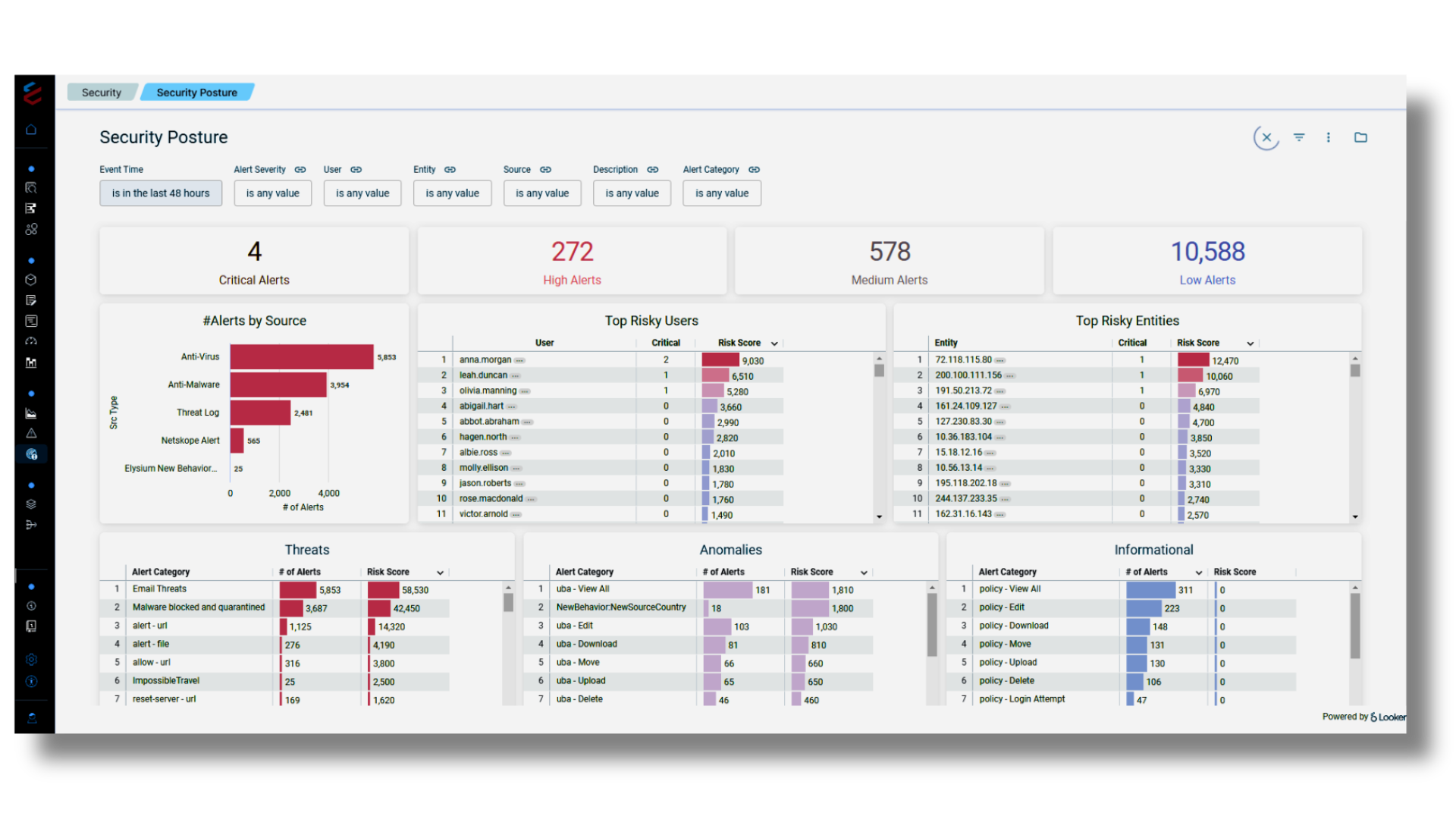
Security Posture
360 View of Incoming Alert Data Streams
- Immediately improve your security posture with out-of-the-box detection rules that automatically flag attacker techniques
- Aggregation pipeline inside the Cloud Data Platform to roll up of alerts from the relevant sources
- Reducing alert noise by deduping repetitive alerts to improve the signal to noise ratio
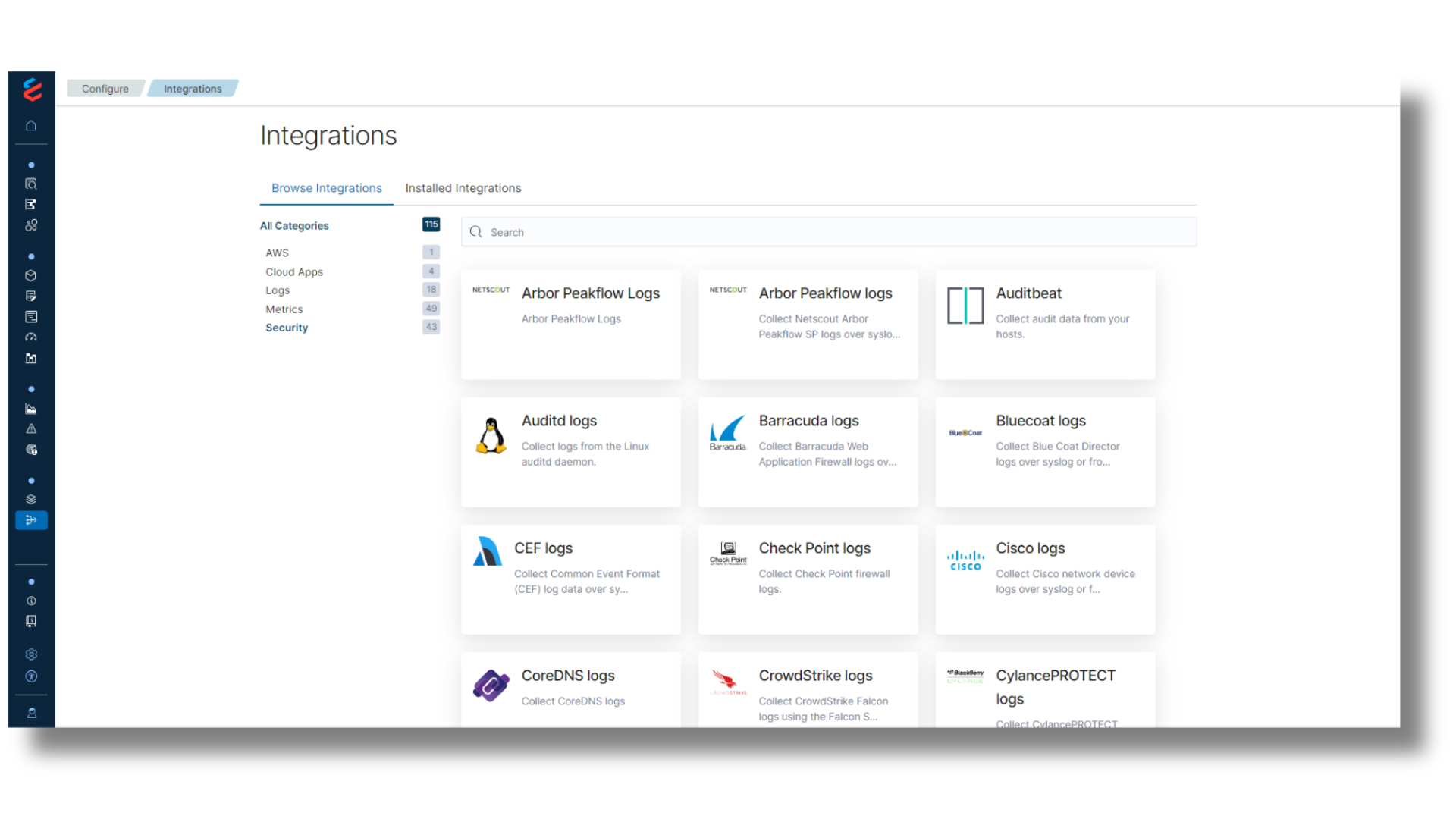
3rd Party Integrations
Turn-key Solution for faster Value
- Unique, high-fidelity intel feds exposing cybercriminal activity
- Fastest access & delivery of intel feds to customers
- Integration with JIRA and ServiceNow for incident management
- Automated responses to threats with Tines Security and other 3rd party tools
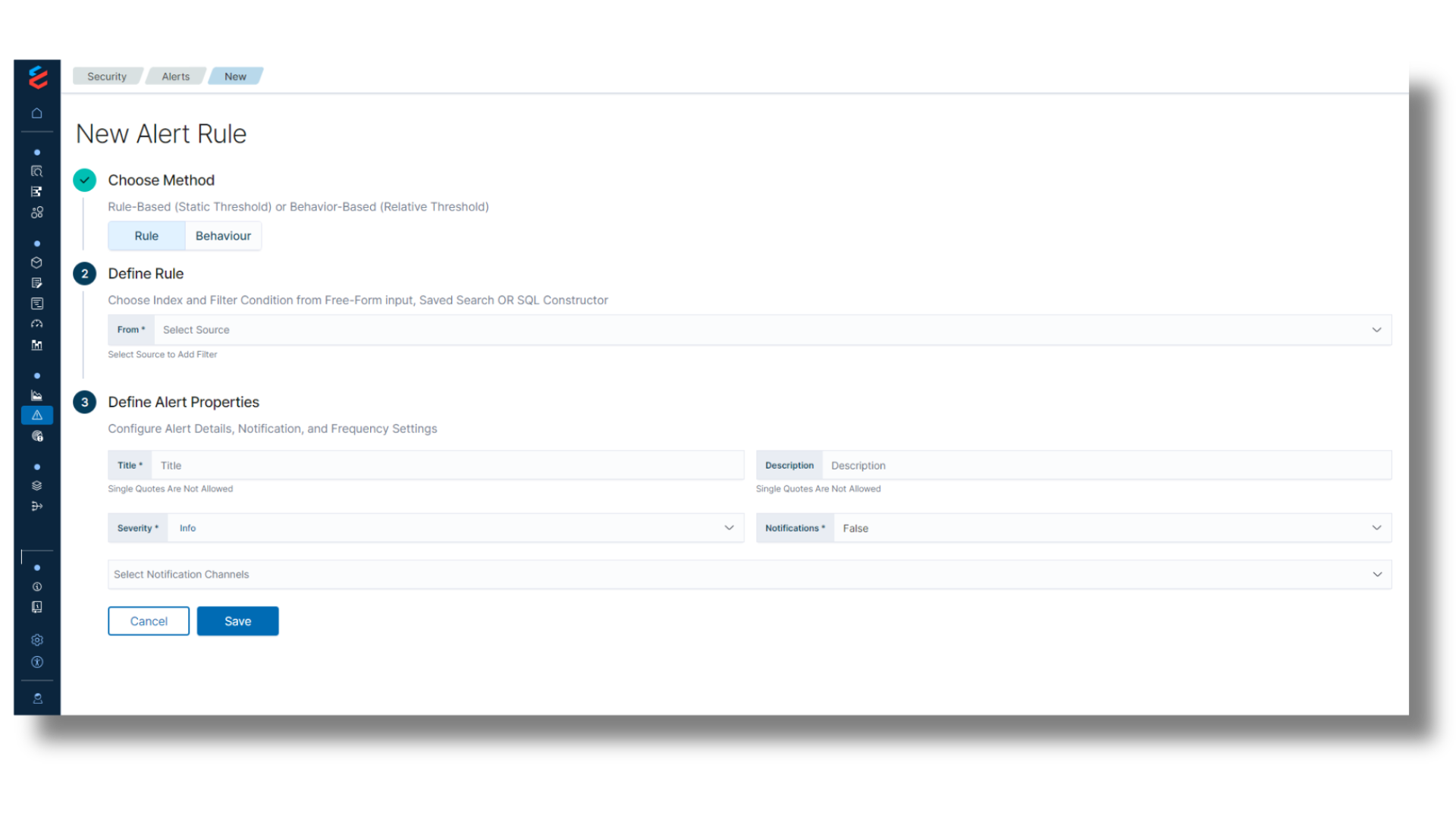
Behavioral and Rule Based Alerts
Keep Current with Quick Notification
- Build advanced alerts based on multiple queries and trigger conditions
- Employ alert recommendations that use supervised machine learning to accelerate response
- Stay notified via Teams, JIRA, and other notification apps
- Easily create your own custom rules in seconds—without the need to learn a proprietary query language
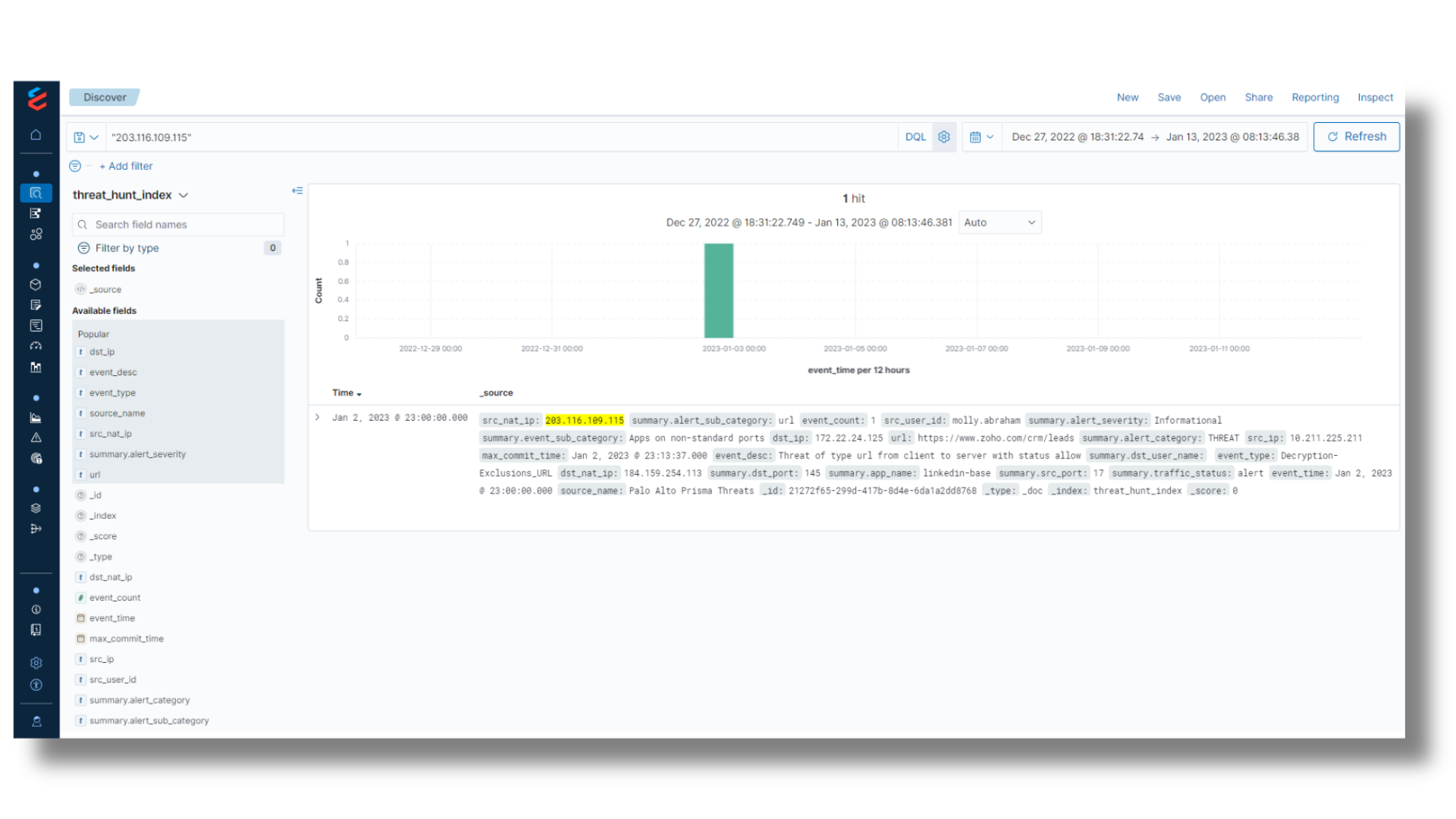
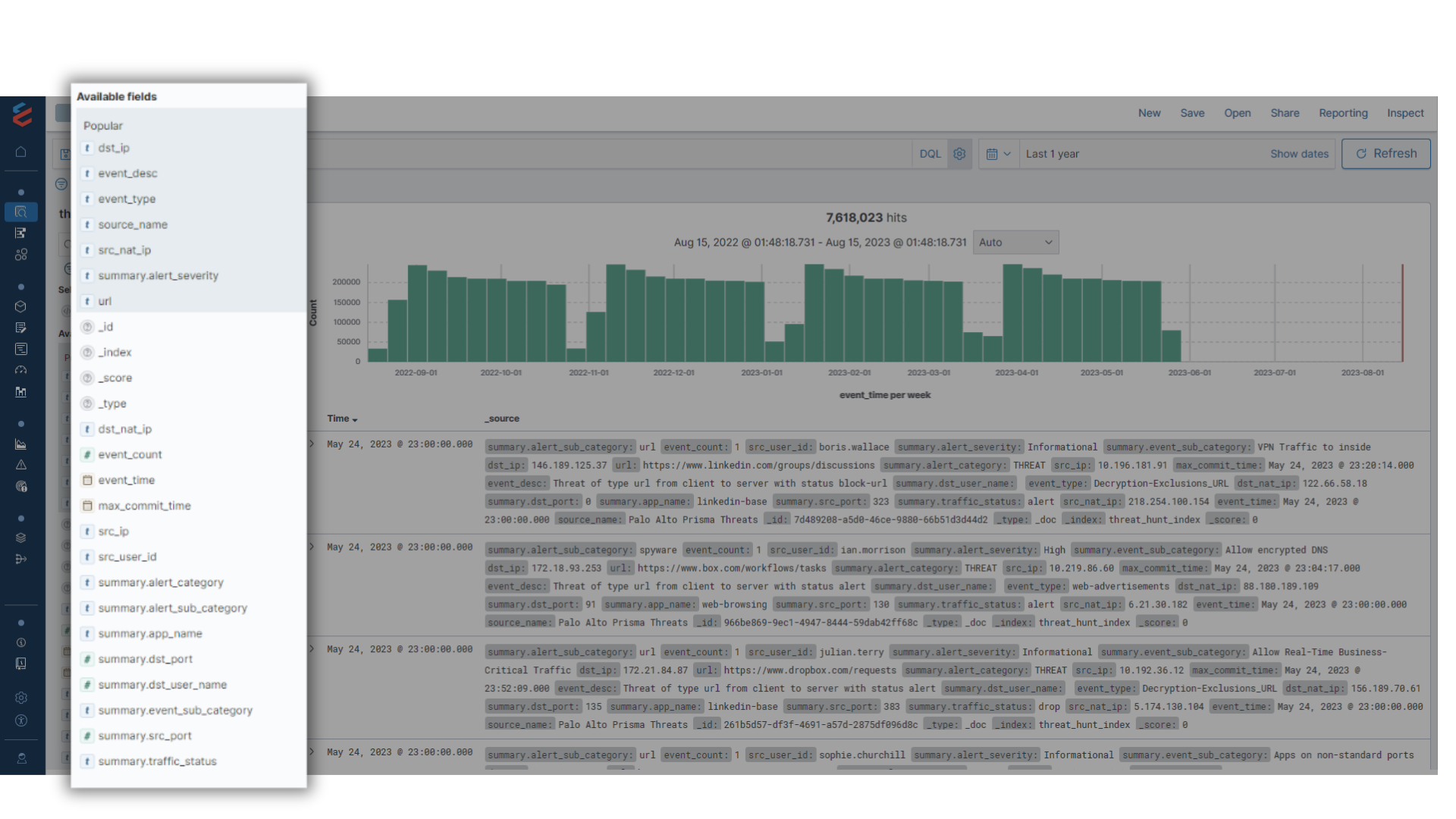
Threat Hunting
Accelerating SecOps by 10x
- Semantic data model to unify the data in terms of field names and values across the sources
- Aggregate index for long range queries over 12+ month periods
- Deduping the data to remove noise with repetitive and recursive messages
- Fast performance with Cloud Data Platform Search Optimization
- Enrichment of the data with missing details (user account, internal IP, last owner, etc.)