A scalable Search, Security and Observability solution powered by opensource tools on commercial cloud data platforms
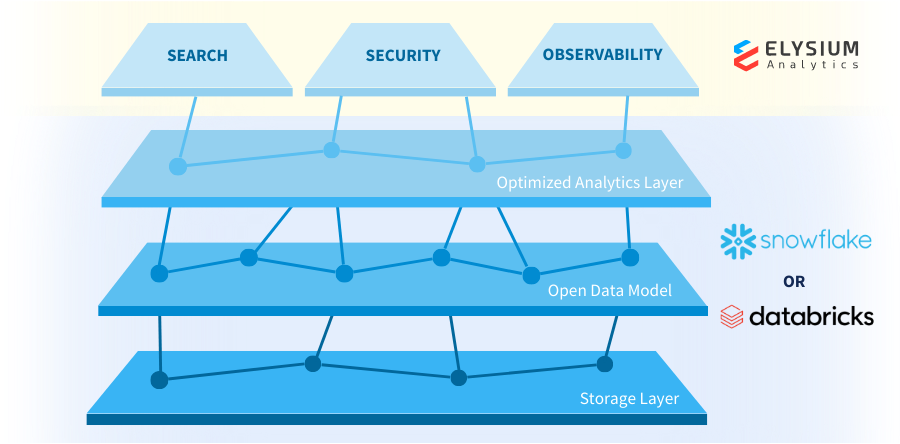
Elysium Cloud
Bring all your data together
Our open data model brings together all security-related telemetry into a unified taxonomy that can detect and understand threats more effectively than before, leading to shorter dwell times. Create analytics models with rich context of user and entity behaviors.
Democratize your data
Our open data model enables downstream analytics for sharing and reuse of threat detection models, algorithms, and analytics. With our high-level abstraction, no specialized data science skills are required to access data productively
Unified view
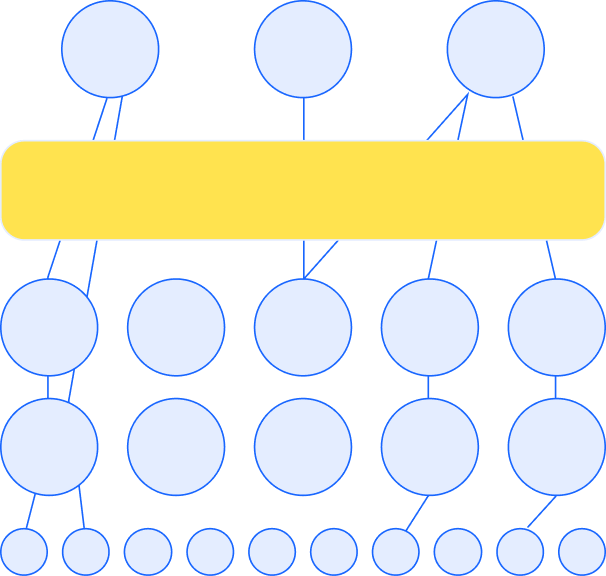
Gain additional insights into user activity. With contextual data connection, an analyst can see the complete flow of all entities connected to this user and understand the severity of the “finding” as well as entities impacted through it.
Single data store
Storing all your telemetry in a single data store gives you instant access to the data across all sources. Do full-text search, use our analytics applications, build your own, or integrate third-party solutions.


Context
Establish context across all your telemetry and enrichment data for a deeper understanding of security threats
Add new sources
New data sources can be added with no impact on downstream applications. New data will be added to the data model and mapped to existing taxonomy, eliminating overhead associated with adding new data sources on legacy solutions.