With most SIEM solutions, you will be facing issues with scaling compute and storage as your data volume grows. In addition to high license fees, the cost of configuring, managing, and monitoring the solution adds overhead, and keeping up with adding more storage and compute gets costly very quickly.
Today, leading companies are solving these problems by augmenting their SIEM and adopting a Snowflake security data lake as the single place for all cyber security analytics and compliance data. With Snowflake’s cloud-built, multi-clustered shared data architecture, you can efficiently store years of semi-structured log Insights and log data, and scale compute resources up or down, automatically or on the fly, to meet the needs of your security analysts. Storing all your log data in a security data lake gives you full visibility to investigate the timeline of an incident across the full breadth of your high-volume log sources, including firewalls, servers, network traffic, AWS, Azure, GCP, and SaaS applications. Being a fully managed, near-zero operations platform, Snowflake gives security analysts the opportunity to focus on performing security investigations rather than spending valuable time managing infrastructure.
By combining a best-practice security data lake platform with full-text search, any information—structured and unstructured—can be retrieved from billions of log lines. With the best aspects of Snowflake and the OpenSearch Dashboards interface, you have an easy-to-use and scalable search solution.
Download the data sheet to get detailed insights on how to increase ROI with Search on Snowflake
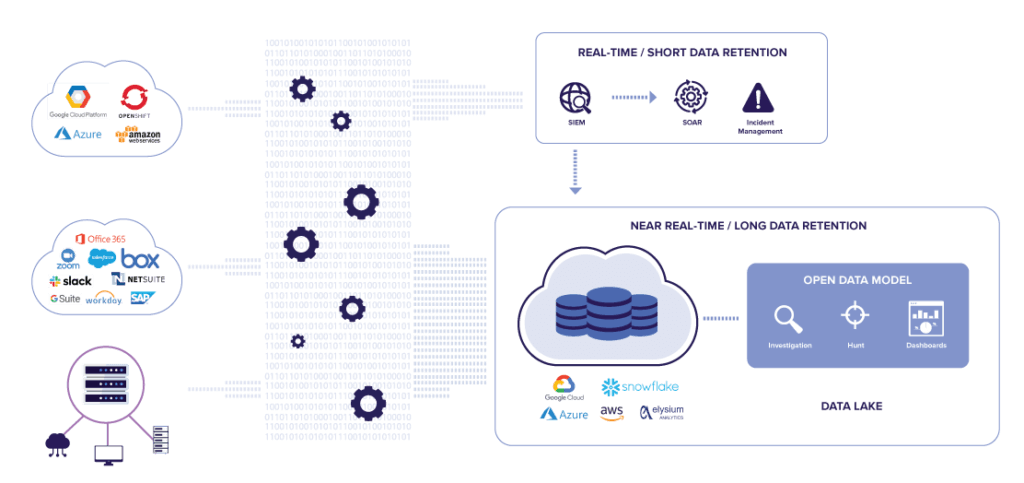
Implementing a security data lake for instant access to historical log data allows you to reduce SIEM costs. Send only data from high value log insights to your SIEM solution, and stream data from all logs to your security data lake for long term retention. This leads to significant savings on license fees, storage cost, and operational overhead, while also meeting compliance requirements.
How to Search Your Log Analytics Data
With the familiar OpenSearch dashboards, also known as Kibana, interface, you can interactively search and explore your data with a pre-defined index pattern by simply entering your search criteria with KQL standard query language in the Query Bar. With the pre-configured index pattern, you can interactively explore your data in Discover, analyze your data in charts, tables, gauges, tag clouds, and more in Visualize.
When submitting a search request, the histogram, Documents table, and Fields list are updated to reflect the search results. The total number of hits, or matching events, is shown in the toolbar. Sort the table by the values in any indexed field.
The Documents table shows the first 500 hits. By default, the hits are listed in reverse chronological order, with the newest documents shown first. You can reverse the sort order by clicking the Time column header. You can also sort the table by the values in any indexed field.
How to Load Your Log Data
Setting up data ingestion is often a time consuming and challenging task when you have multiple sources of log data from cloud and on-premises sources.
We have made the process of collecting, parsing, enriching and loading your data simple. For data you are already loading to your SIEM or log management solution, we will configure the data collection implementation enabling it to write logs directly to Elysium Analytics open data model on Snowflake while maintaining the data flow to your legacy applications in parallel with zero disruption to existing solution.
If you are not collecting log insights data for log analysis today, we will set you up and handle everything for you from end to end.
Download the data sheet to get detailed insights on how to increase ROI with Search on Snowflake
About Elysium Analytics
Elysium Analytics is a security data lake for modern enterprises with complex infrastructure who are challenged by data silos, data overload, and increasing cost of data retention and recognize the value of a security data lake with an open data model for threat investigation, hunting, and monitoring. The Elysium Analytics solution is a turnkey open data model on a security data lake with applications and tools that provides for faster investigations and more efficient threat hunts and monitoring at cloud scale with significantly lower cost. Unlike legacy solutions, our product leverages Snowflake for cloud platform benefits, eliminates data silos and provides full visibility of log data. Our solution integrates with existing SIEMs and security tools.